Introducing Wasmcov: Code Coverage Tool for Wasm Projects
We’re proud to introduce Wasmcov, a specialized code coverage tool tailored for Wasm environments.
🇺🇦 Hacken stands with Ukraine!
Learn more
So you have just familiarized oneself with the three steps of how to become a white hat hacker and now wonder what ethical hackers actually do? Then, we have a nice story for you.
On May 22, 2018, one of Hacken’s own advisors Oleksii Matiiasevych helped to prevent a massive crisis in a great crypto marketplace.
He personally saved $1.5 million during the Parity wallet vulnerability exploit. Recently, he proved his white hat again by identifying a vulnerability that 8 top-rated cryptocurrency exchanges were susceptible to.
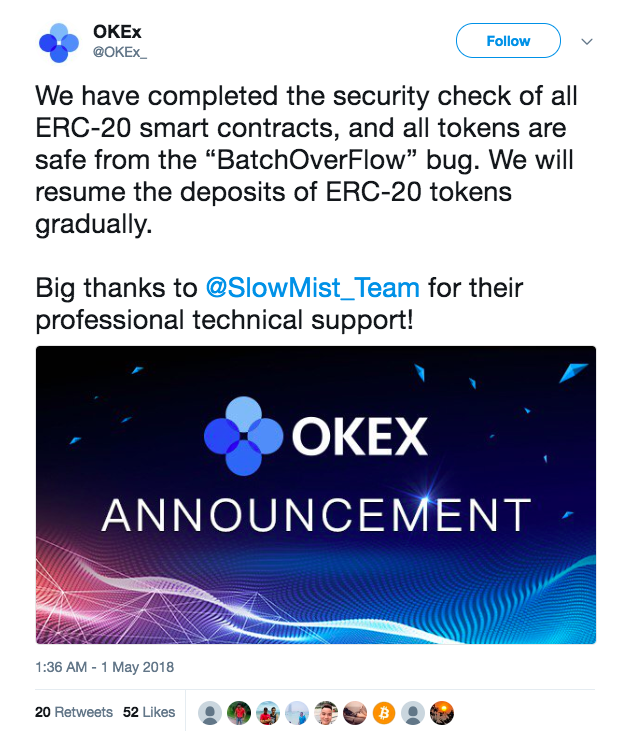
A few weeks ago, it was reported that that a number of well-known crypto-exchanges contained a batchOverflow bug in multiple ERC20 smart contracts.
In fact, the vulnerability was identified more than a month ago by Matiiasevych. While testing different cryptocurrency exchanges, Mattiasevych identified this vulnerability and confirmed that it could be exploited to withdraw arbitrary ill-gotten amounts of ETH and other cryptocurrencies from vulnerable exchanges. The white hat hacker assumed that the problem is in the deposits processing code.
The tests carried out show that at least 8 well-known centralized exchanges have this bug. However, Matiiasevich noted that decentralized exchanges that don’t have a hot wallet/pool are not affected. Together with Ambisafe, Giveth platform, and the community of white hackers Matiiasevich compiled a detailed report called “ETH/ETC Deposits Processing General Security Breach Report” with recommendation on how to eliminate the vulnerability.

In the report, it is noted that this attack will be successful for ETH and ETC, but also can be relevant for a number of forks, especially for coins such as UBIQ, EXP, POA, TOMO, and ELLA.

“We reported this to all the exchange platforms where this vulnerability was discovered. After that, we sent our report to almost 200 exchanges, which could also be potentially vulnerable; thus, it seemed that we did everything we could.”
However, the next day, Matiiasevich realized that hackers might have another way to take advantage of that vulnerability.

In the report, the developers recommend to stop accepting deposits in ETH and ETC and carefully study the processing code by converting the flat list of traces of internal transactions into a nested list. Afterward, a number of actions were necessary to take in order to eliminate the problem. In addition, there were also given a few recommendations on how to get rid of the second method of exploiting the vulnerability.
The vast majority of exchanges made public comments concerning the bug. They announced to suspend ERC20 token trading until the circumstances are clarified.



“Today, the word ‘hacker’ has gained a new, positive connotation. The white hat hackers, such as Oleksiy Matiiasevich, report bugs with the aim to make the crypto world safer. We all should thank developers for contacting vulnerable crypto exchanges and assisting them in resolving the issue. Coinbase showed a great example that exchange should take care of their clients by reacting immediately to the identified vulnerabilities. Cybersecurity matters.”, — Dmytro Budorin, CEO of Hacken.
Read about different types of hackers and learn who script kiddies are
If you support the course of actions Matiiasevych took and want to practice ethical hacking too, you can always try your hacking skills on special platforms called bug bounty. The only thing you need is to register on HackenProof and start earning your bounties for disclosed vulnerabilities.

















